Certificate Reader

Ahhh certificates. Sometimes is hard to find information about them or where to use them.
I will show you a tool I use often to extract the Base64, JSON Web Key and the private key from a certificate.
Why you might ask? well, if you have used an API lately, you will probably find it secured by a JWT (JSON Web Token).
You can find more information about what a JWT is here.
But long story short, we pass a token to the API that we obtained from an Identity Provider (Duende, Ping Federated, OKTA, etc.) in order to authenticate our request.
First you will need a certificate to test the tool, you can use this powershell script to generate the cer and the pfx
$certname = "myselfsignedcert" ## Replace {certificateName}
$cert = New-SelfSignedCertificate -Subject "CN=$certname" -CertStoreLocation "Cert:\CurrentUser\My" -KeyExportPolicy Exportable -KeySpec Signature -KeyLength 2048 -KeyAlgorithm RSA -HashAlgorithm SHA256
Export-Certificate -Cert $cert -FilePath "e:\certs\$certname.cer" ## Specify your preferred location
$mypwd = ConvertTo-SecureString -String "myPassword" -Force -AsPlainText ## Replace {myPassword}
Export-PfxCertificate -Cert $cert -FilePath "e:\certs\$certname.pfx" -Password $mypwd ## Specify your preferred location
You can obtain a JWT by sending a request to the Identity provider with simple client credentials and secret, but that is considered not enough anymore.
Now what you do is to sign the request with a certificate and obtain the JWT.
In another post I will show you how to setup Duende and Postman in order to secure your API, but for now I will show you how to install the tool using Docker.
If you don't use Docker in your development, please use it. Â It speeds up dev and you can do so many cool stuff with it.
Assuming you have docker desktop installed on your machine or on a server somewhere.
Pull the image.
docker pull jtenorio/jtcertificatereaderweb:latest
Run the container.
docker run -d -e ASPNETCORE_URLS=http://*:4040 -p:4040:4040 -e IsOverrideBasePath=true -e OverridenBasePath=/certreader jtenorio/jtcertificatereaderweb
Docker Hub Link
The p flag will map a specific port for the container, and it must match the ASPNETCORE_URLS port.
The IsOverrideBasePath is used when a reverse proxy is used (NGINX), its intention is when the site is on a different location, the ~ in MVC will resolve correctly.
The OverridenBasePath is used to map the base path when in a reverse proxy.
If you don't want to install it, you can use it from
https://darthseldon.net/certreader/
The tool takes only 2 parameters.
A PFX (Public and Private) or a CER (Public) file that contains the certificate.
The password, if it is a PFX file.
When you submit, you will see a similar result to this
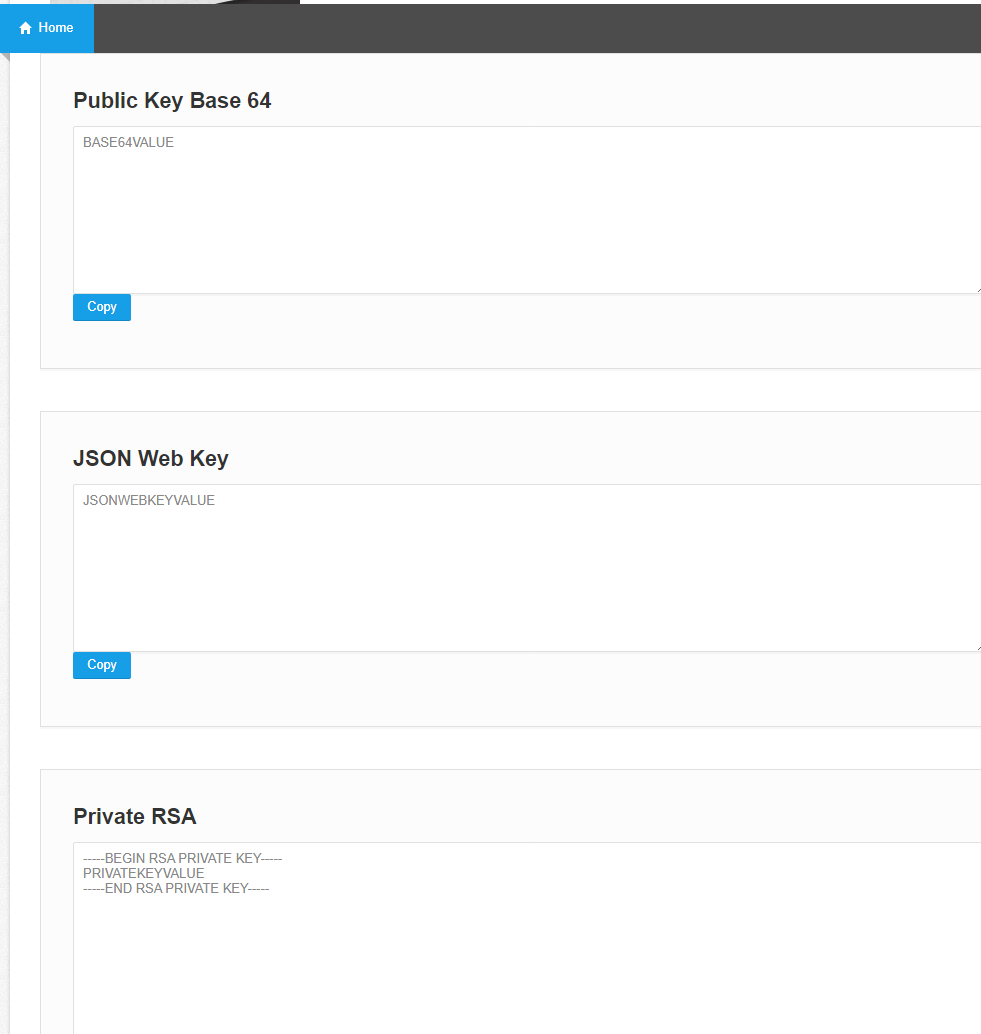
You can copy the values and use them.
On the next installment I will go thru the code and explain what is happening behind the scenes.
Happy hacking!!!!